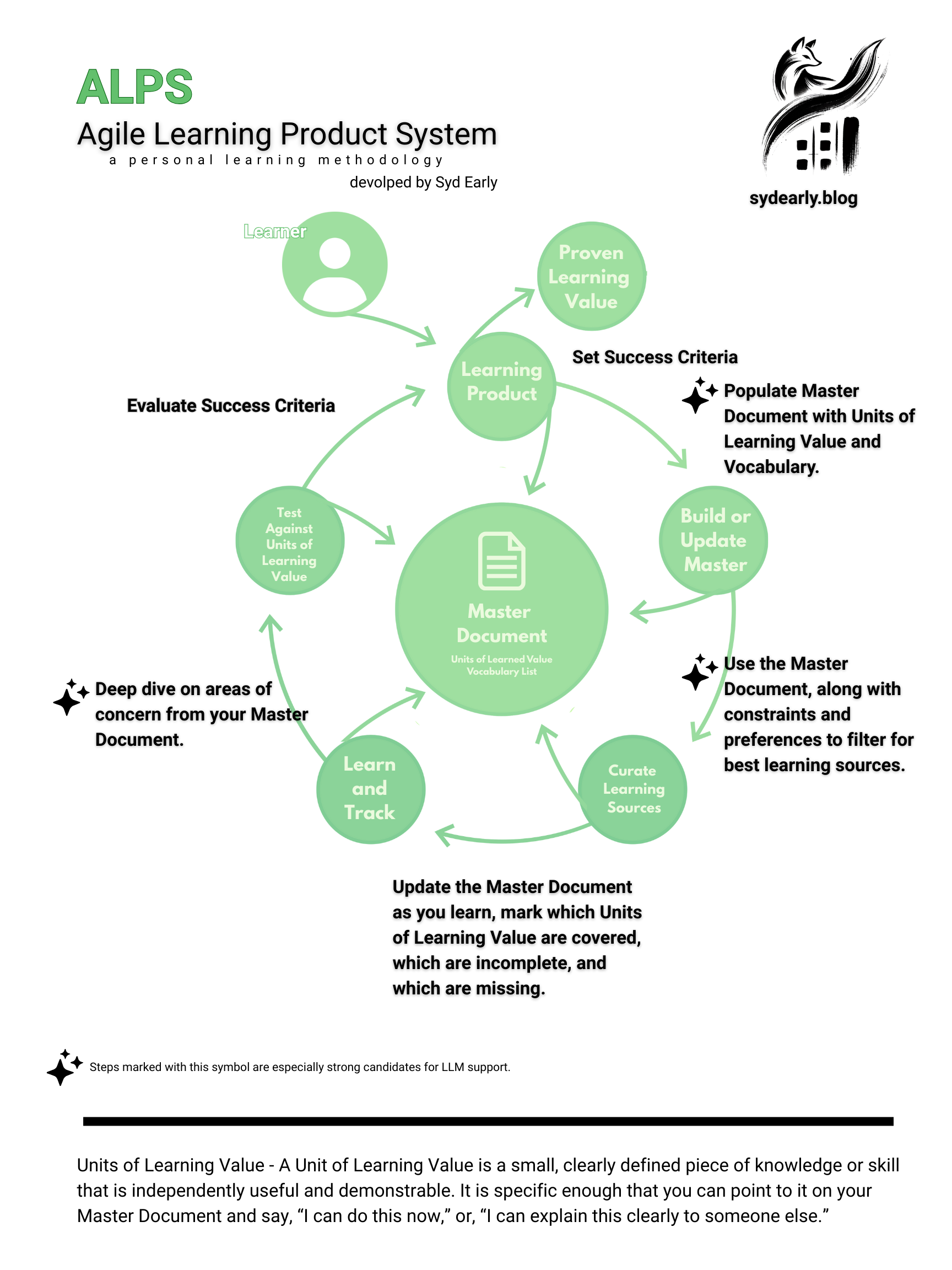
Purpose
This process creates a signed affidavit that cryptographically binds a SHA-256 hash of a digital artifact to a verifiable GPG identity, enabling independent verification of integrity and authorship without asserting factual truth.
This is useful for publishing essays, research notes, creative work, datasets, or any digital artifact where you want to demonstrate:
- The file has not changed since a specific moment in time
- A specific cryptographic identity controlled the signing key
- Verification can occur independently, without contacting the signer
Threat Model (What This Does and Does Not Do)
This process proves:
- File integrity (tamper detection)
- Control of a specific GPG private key at signing time
- A clear, auditable chain of verification
This process does NOT prove:
- The truthfulness of the content
- The authenticity of events depicted
- That manipulation did not occur before hashing
This is an integrity and authorship signal, not a claim of objective truth.
Signing Process (Author / Publisher)
0) Preconditions
- The content file is finalized
- You already have a GPG key
- You will not edit files once hashing begins
1) Capture Artifact Details (for the affidavit)
stat -f "%N
Size (bytes): %z
Permissions: %Sp
Owner: %Su
Group: %Sg
Created: %SB
Modified: %Sm
Inode: %i
Device: %d
" "<file_name>" > file_details.txtThis records filesystem-level metadata at the moment of signing.
The output will be embedded into the affidavit, then discarded.
2) Create affidavit.txt
vi affidavit.txtAffidavit Template
------------------------------------------------------------
AFFIDAVIT OF DIGITAL CONTENT INTEGRITY (SHA-256 + GPG SIGNATURE)
------------------------------------------------------------
I, <Full Legal Name>, declare under penalty of perjury that:
1) I am the creator or lawful custodian of the digital file(s) referenced below.
2) On <YYYY-MM-DD> at approximately <HH:MM> (<Time Zone>), I computed SHA-256 hashes
for the file(s) listed in this affidavit.
3) To the best of my knowledge, the file(s) referenced have not been altered since
the hashes were computed. Any modification would result in a different SHA-256
hash and cause verification to fail.
4) I am signing this statement using my GPG private key. The corresponding public
key fingerprint is:
<YOUR FULL KEY FINGERPRINT>
Referenced Files:
- <file_name>
- affidavit.txt
- hashes.sha256.txt (hash manifest)
Executed on: <YYYY-MM-DD>
Location: <City, State, Country>
Signature:
<Full Legal Name>
<Contact info optional>
------------------------------------------------------------
File Details (observed at time of signing)
------------------------------------------------------------
<PASTE file_details OUTPUT HERE>
------------------------------------------------------------After pasting the file details, delete file_details.txt.
3) Create the Hash Manifest
Include both the artifact and the affidavit:
shasum -a 256 <file_name> affidavit.txt > hashes.sha256.txt4) Sign the Affidavit (Detached Signature)
gpg --armor --detach-sign affidavit.txtProduces:
affidavit.txt.asc5) Sign the Hash Manifest (Detached Signature)
gpg --armor --detach-sign hashes.sha256.txtProduces:
hashes.sha256.txt.asc6) Export the Public Key
gpg --armor --export "user@email.com" > user-publickey.ascFinal Evidence Bundle
Distribute these files together:
<artifact_filename>affidavit.txtaffidavit.txt.aschashes.sha256.txthashes.sha256.txt.asc<signer>-publickey.asc
Verification requires only GPG and SHA-256 tools.
Verification Process (Independent Verifier)
0) Preconditions
- You have received the full evidence bundle
- The bundle contains:
<artifact_filename>affidavit.txtaffidavit.txt.aschashes.sha256.txthashes.sha256.txt.asc<signer>-publickey.asc- GPG and
shasumare installed - You trust the public key source or can verify its fingerprint independently
1) Import the Signer’s Public Key
gpg --import <signer>-publickey.asc(Optional but recommended)
gpg --fingerprint <signer-email-or-key-id>Confirm the fingerprint matches an independently published reference.
2) Verify the Affidavit Signature
gpg --verify affidavit.txt.asc affidavit.txtExpected output:
gpg: Good signature from "<Signer Name> <email>"3) Verify the Hash Manifest Signature
gpg --verify hashes.sha256.txt.asc hashes.sha256.txtExpected output:
gpg: Good signature from "<Signer Name> <email>"4) Verify File Integrity
shasum -a 256 -c hashes.sha256.txtExpected output:
<artifact_filename>: OK
affidavit.txt: OK5) Manual Review
Open affidavit.txt and confirm:
- Signer identity
- Public key fingerprint
- Listed files match the bundle
- File details match the received artifact
- Date, time, and location align with expectations
6) Interpretation Guidance
A successful verification confirms:
- The files have not changed since hashing
- The affidavit has not changed since signing
- The signer controlled the private key used
It does not confirm:
- Truthfulness of the content
- Authenticity of depicted events
- Absence of manipulation prior to hashing
Closing Note
This process is intentionally modest in scope.
It does not attempt to establish truth, only integrity, authorship, and verifiability.
In an environment increasingly shaped by synthetic media, these signals matter.
They are not sufficient on their own, but they are necessary.